Managed Identities and Permissions
- Mark Webb
- Jul 2, 2025
- 3 min read
It's been a while! Thought I'd get back on the blogging trail by writing about something I came across recently which puzzled me for a little bit before I worked out what was going on. I might be showing my lack of knowledge of all things Entra/Graph and permissions here but ah well....if it's useful for someone I'll take it.
I was looking at moving permissions for a Logic App step from a service account connection (bad security) to a managed identity connection (good security).
The permission(s) I was working with was around creating/amending/deleting M365 groups and I didn't want to have the connection using a full blown User Admin type Entra role as that was over permissive. So I'd created a custom role with just the permissions the connection needed, in this case these:

All well and good. I assigned this custom role to my service account and no issues, Logic App steps worked no issue.
Logic App step

and the output showing the group has been created without any issues...
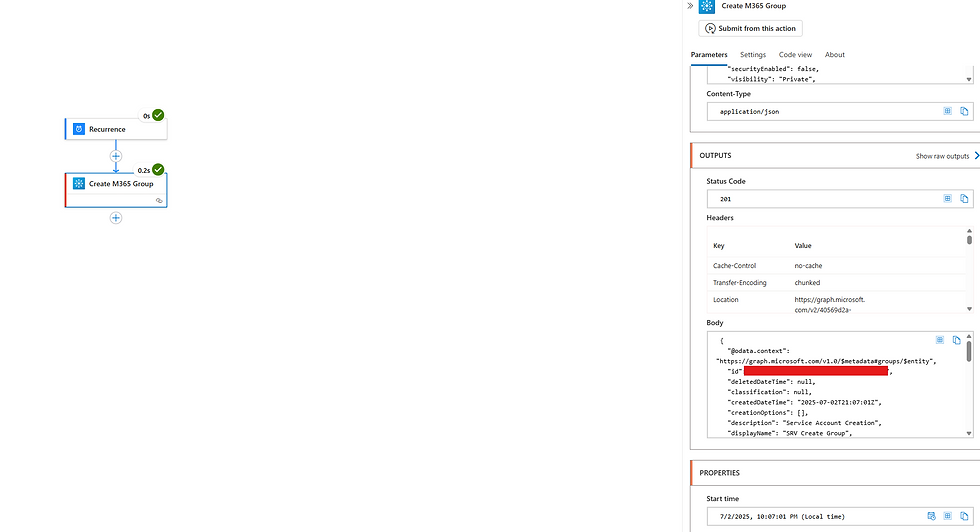
I then wanted to move this connection over to the System Assigned Managed Identity of the Logic App to increase security. I thought nice and easy, enable the identity, assign it the same custom role and voila.....and that worked fine for creating an M365 Group

however....when we try and delete a group.....
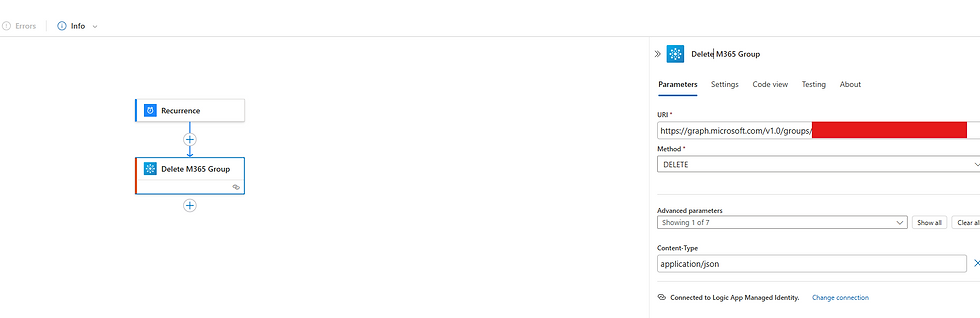
we get an error telling us we don't have permission

Puzzled me as the Managed Identity has the same permissions/role as the service account did and the create request worked fine.
After a fair bit of googling and a little help from Copilot pointing me in the right direction I worked out that there was a difference in how the two requests were being handled in the back end.
For a service/user account the custom role with relevant permission is enough however for the Managed Identity it also must have the required Graph permission to carry out the task. I can't easily find a Microsoft document that explicitly describes this but it seems like it's around how the account (service account or Managed Identity) is authenticating and the claims it receives back from Entra/Azure.
So what we need to do is grant the Managed Identity the Graph permissions. This has to be done via PowerShell, not something that can be done via the GUI. Example script below to assign the Group.ReadWrite.All permission to a Managed Identity. Replace ServicePrincipalId with the object Id of the Managed Identity.

Once done, we can see the permission has been granted to the Managed Identity

Now...if we run the Logic App again we get a successful response.

Same principle will apply to other types of group changes we want to make such as updating group memberships etc.
One other thing I noticed was that we also can't use the built in actions for the requests either. For example, if we wanted to add a member to a group normally we'd use this action
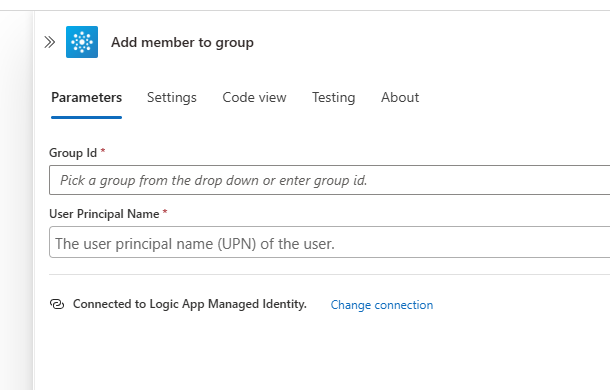
and just add the Group Id and the UPN of the user we want to add. For some reason, even though the Managed Identity has the right Graph permissions now this still fails with a weird error

Turns out that now...we have to provide the Object ID of the user not the UPN. I assume this is again because the Managed Identity is authenticating/making the request in a different way than a service/user account and using a Graph request.
As well as that, we can't even use this built in action any more. Even adding the Object ID to the "User Prinicpal Name" produces the same error

So we have to use the "Send a HTTP request V2" action with the Office 365 Groups section

Provide the releavnt URI, method and body and then finally it works!

That seemed like a lot of effort for what I thought would be a very simple change to make.
It might be there's some documentation out there that explains this in simple terms but I couldn't seem to find it and as usual, the error messages you get aren't the best and don't easily point you to what you've got wrong.
I'm not sure if this is just a consequence of wanting to make the permissions granular for this Managed Identity and whether I'd get the same issue if I'd just given it one of the built in Entra roles (User Admin for example).
Managed Identities are a much more secure method to grant permissions to your workloads, it'd be nice to make it easier to understand any differences in their behaviour compared to other methods and maybe also be able to grant Graph permissions via the Azure portal in the same way we can for App Registrations.
Hopefully this is useful for someone and I don't just get a lot of comments saying "uh, yeah. Everyone knows this"


Comments